Lesson 2: Common Threats to Personal Information

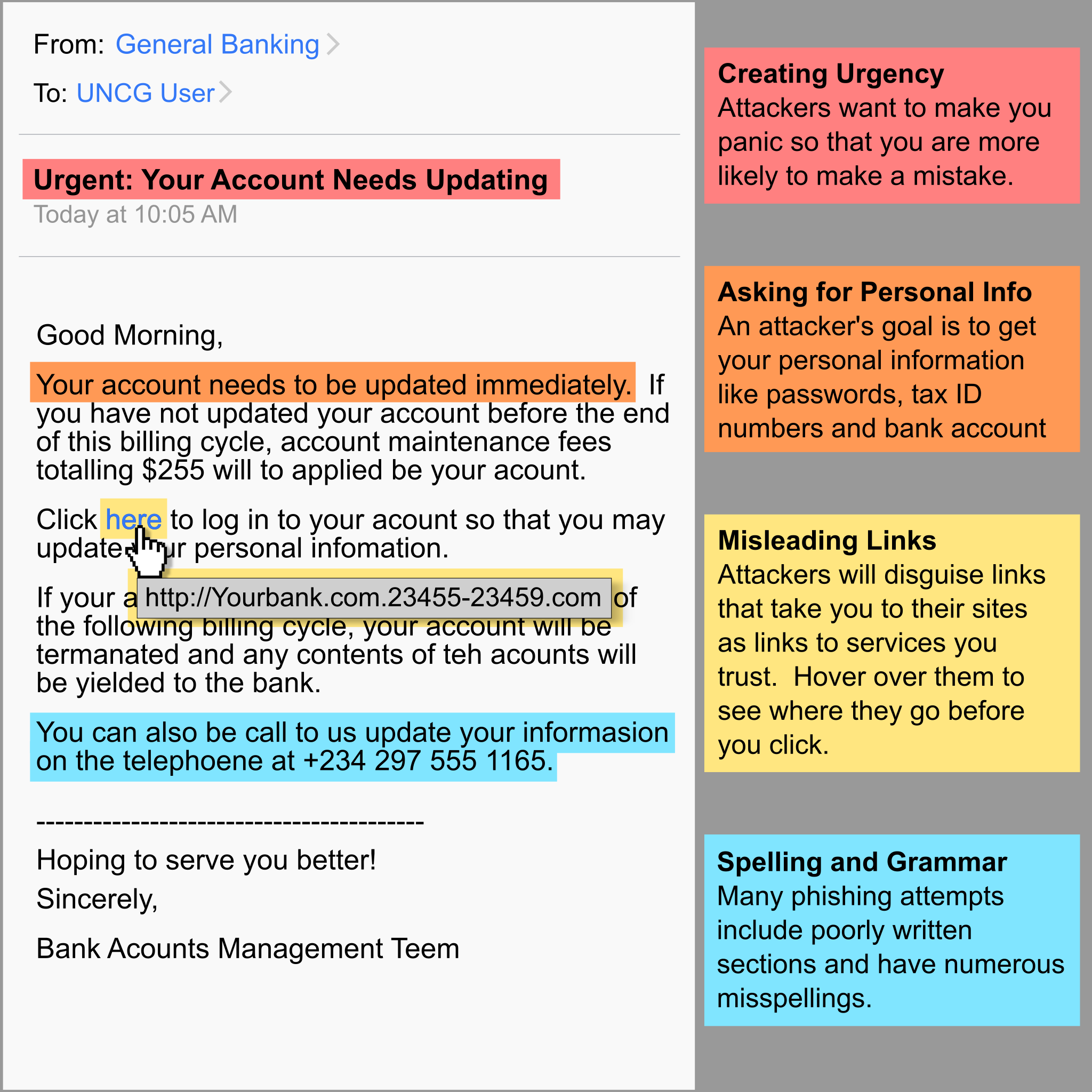
Phishing attacks occur when an attacker attempts to acquire personal information, such as credit card numbers, passwords, and personal data, by disguising themselves as a legitimate company or individual through fraudulent emails or websites. To perform a successful phishing attack, the attacker typically creates an email or malicious website that appears to be from a legitimate and authentic source. These fraudulent emails and websites may contain links that direct the user to a malicious website, or may contain malicious attachments that can infect the victim’s computer and extract private data.
In general, there are two primary methods used by attackers to phish for information: email scams and fake websites. Email scams typically involve spammers sending out emails that may appear to be from a legitimate company. The email may try to lure the recipient into clicking a link that redirects them to a malicious website or to open a malicious attachment. Fake websites may also be used, as attackers can easily spoof legitimate website addresses to trick victims into visiting websites disguised as authentic sites.
For example, Equifax, one of the nation’s largest credit bureaus, was a victim of a phishing attack in 2017. The attackers set up a false website that appeared to be from Equifax and tricked visitors into providing their personal information for identity theft. Millions of customers had their personal data compromised. Other companies that have seen their customers become victims of phishing attacks include Google, Facebook, and Microsoft.