The Rise of Fake Landing Pages
Phishing attempts have become increasingly sophisticated, with cybercriminals creating fake landing pages that closely mimic legitimate websites. These deceptive pages are designed to lure unsuspecting users into divulging their personal information, such as login credentials and credit card details. Often, these fake pages are nearly indistinguishable from the real ones, complete with authentic-looking logos, fonts, and layouts. It is crucial for users to be vigilant, checking URLs carefully and ensuring that they are on a secure (https) site before entering any sensitive information.
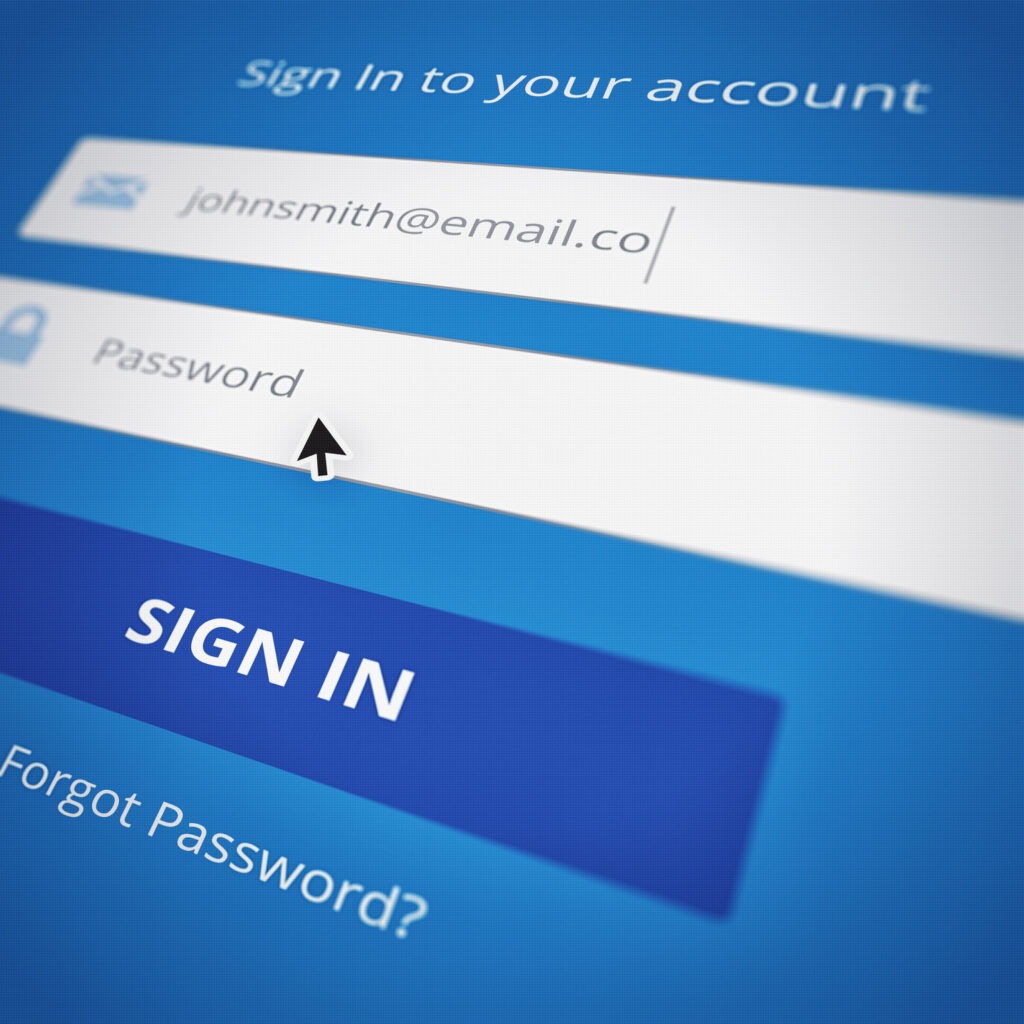
Beware of Fraudulent Login Portals
One of the most common tactics used in phishing schemes involves fake login portals. These bogus sites request users to enter their login details, which are then captured and used maliciously. Cybercriminals often create these portals by sending emails that emulate trusted services, urging recipients to “verify” or “update” their information. Users must exercise caution and avoid entering personal data unless they are certain of the site’s legitimacy, often achievable by accessing the site directly rather than through emailed links.
Deceptive User Profiles on Social Media
Social media platforms have also become fertile ground for phishing attacks via deceptive user profiles. Attackers create fake profiles that impersonate real individuals or reputable entities to gain the trust of potential victims. These impersonated profiles might send friend requests or direct messages that contain malicious links leading to phishing sites. Users should scrutinize unfamiliar profiles, verify the identity of the sender through secondary means, and avoid clicking on unsolicited links.
“Phishing attempts, often employing fake landing pages, login portals, and deceptive social media profiles, aim to trick users into divulging sensitive information. Recognizing key indicators and adopting protective measures can significantly reduce the risk of these cyber threats.”
Key Indicators and Protective Measures
Identifying phishing attempts requires awareness of key indicators and the implementation of protective measures. Users should look for spelling errors, generic greetings, and inconsistencies in email addresses or domain names as potential red flags. Enhancing security practices, such as enabling multi-factor authentication (MFA) and regularly updating passwords, can help mitigate the risk of falling victim to phishing scams. Additionally, employing anti-phishing tools and staying informed about the latest phishing techniques can provide an additional layer of defense.



